Enter your details below to stay up-to-date with the latest IT solutions and security measures.
There are many fascinating aspects to information security, but let’s face it, logging is probably not one of them. A sometimes overlooked area of system management and security, it’s frequently left unmanaged, constantly over-written and seldom accessed once archived.
It’s time to view logs from a different, more worthwhile perspective.
Logging holds complete event histories for devices across the network – interesting, but unless you have the bandwidth to analyse it, useless.
The smart way to analyse log data.
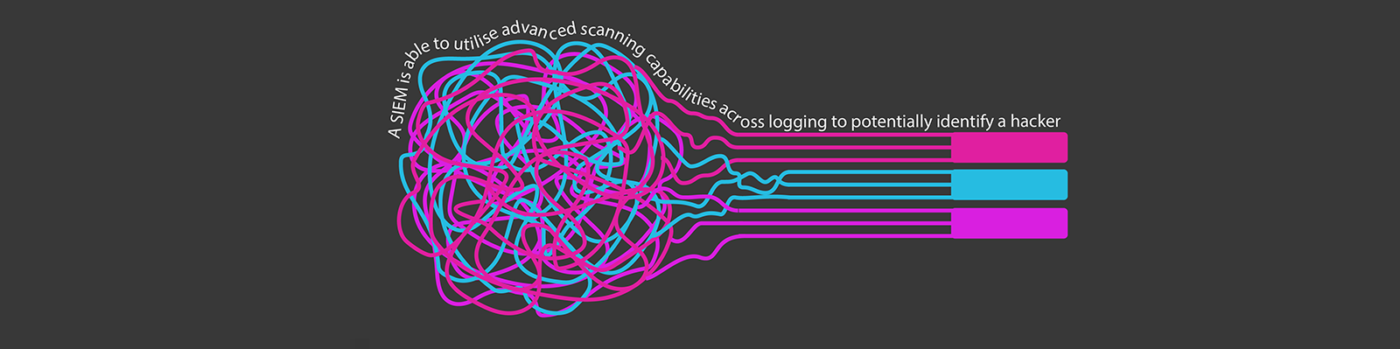
A ‘security information and event management system’ commonly referred to as a SIEM uses advanced scanning capabilities to search across network log data, identifying patterns created by unexpected events. These patterns can alert you of malicious activity within your network. The SIEM can identify unusual behaviours such as those of a hacker in the system who has perhaps, over a long period of time been slowly exfiltrating data from your organisation.
A SIEM will identify and notify you of:
- growth patterns
- shrinkage patterns
- unusual behaviours
I recommend logs are kept for a minimum of one year as this allows the SIEM more scope for identifying data patterns. This will not only provide a clearer view of your current situation, but will also provide a clearer view of the path forward.